
Two Types of acquisition
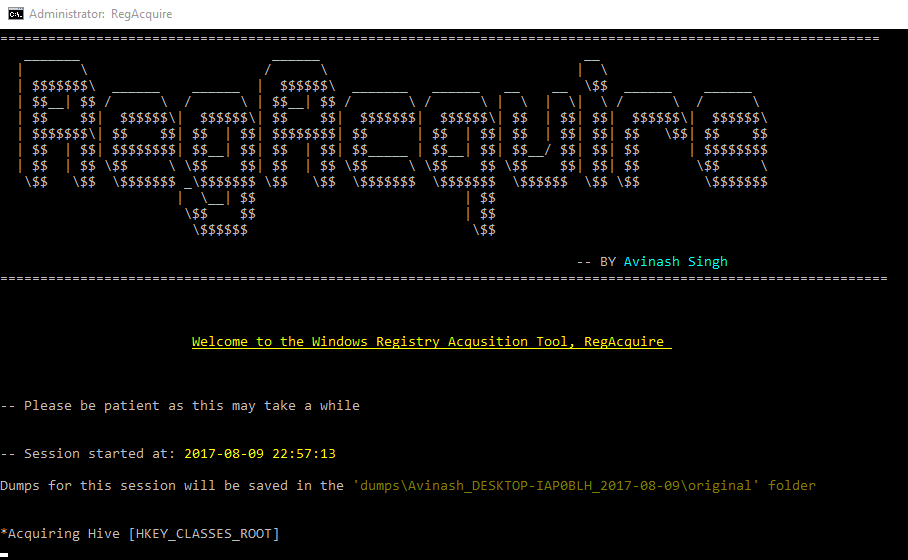
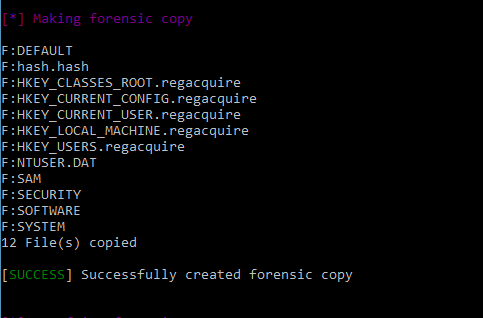
RegAcquire is a batch script that acquires Windows Registry Dumps, it makes use of 2 other programs RawCopy and FCIV(File Checksum Integrity Verifier) for the sake of simplicity the batch script with the neccessary supporting files were built together in a standalone executable.
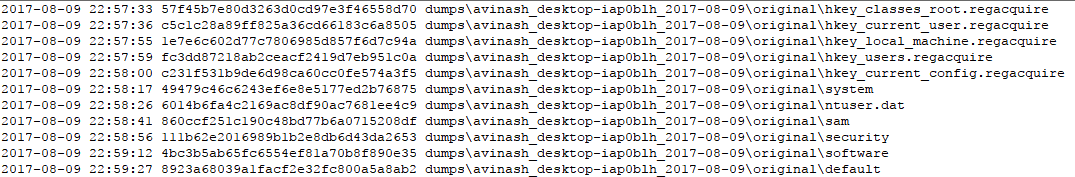
RegAcquire makes use of reg export found built-in in Windows.
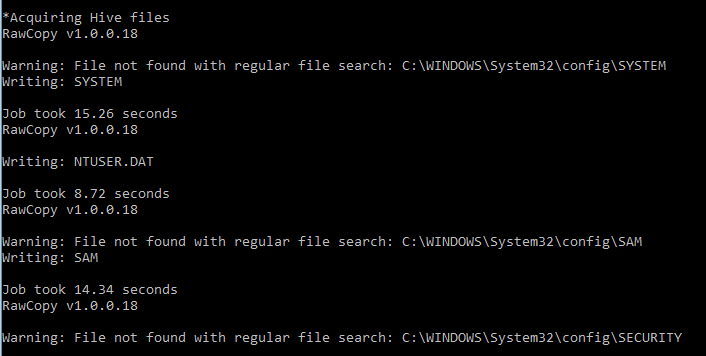
Since reg export strips away some information, RegAcquire also acquires the physical hive files, in Windows system. These files are live files meaning they are constantly in use, thus making it difficult to copy it normally. VSS (Volume Shadow Copy) was used to capture these files using RawCopy.
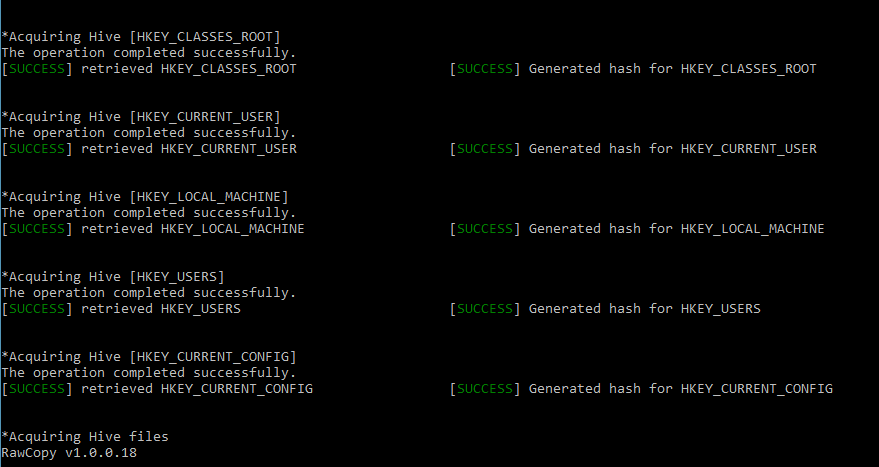
File Checksum Integrity Verifier (FCIV) is used to hash the files as well as check the integrity of the forensic copy. The reason why these other two applications was used is to ensure that they can run on any Windows operating system targeted from Windows 7 and up, and for the reason that all Computers may not have some built-in features that could have been used for this purpose.
Forensically sound
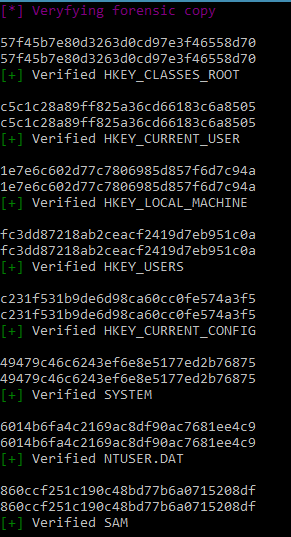
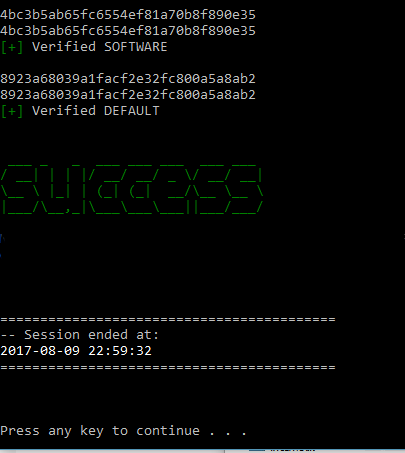
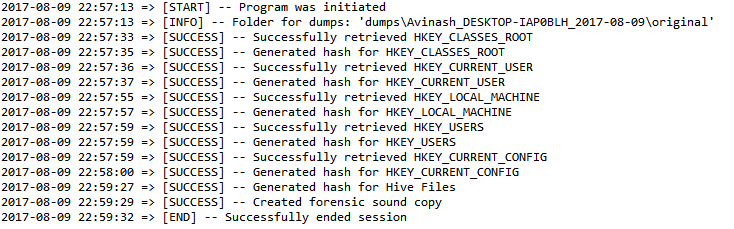
RegAcquire logs each process and creates MD5 hashes of each file for verifiability.
Since the original files are never used in Digital Forensics RegAcquire makes a forensically sound copy by copying the original files, logging each and then further verifying the copy by hashing the files of the copy and comparing them to the original files. The original files are marked as read-only and the hash file has special permissions that doesn't easily give access to anyone to write or modify it. RegAcquire performs two phase hash log to ensure that changes to the files can be detected, this is achieved by logging both in the acquired registry dumps and the entire life span of using the RegAcquire program, this is just a measure for authenticity and is only checked when there are suspicions.